Business
How to Fight a Ransomware Attack

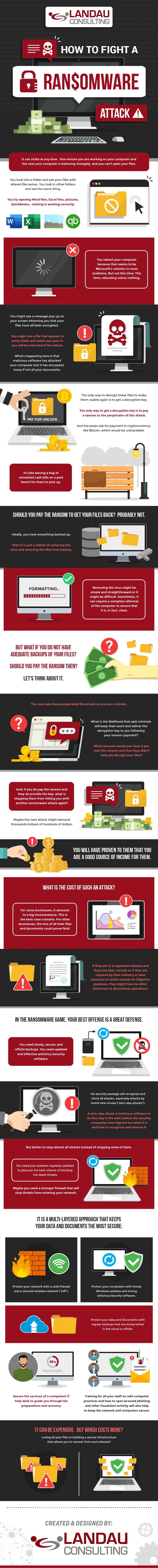
Ransomware is one of the threats that could jeopardize a business, whether big or small. Ransomware is a type of software that gains access to files, systems, and other data and blocks the access of users to these files.
These files then are taken like hostages using encryption, and unless the victim pays for the decryption code, there is no way of opening those files. Usually, transactions are paid via bitcoin or other virtual currencies because of them being untraceable.
Ransomware is so pervasive that in 2017, the Federal Bureau of Investigation’s Internet Complaint Crime Center (IC3) has received 1,783 ransomware complaints with adjusted losses of over $2.3 million. And these are just the reported cases. Many cases go unreported.
A computer can be infected with ransomware through various means like Remote Desktop Protocols that allow computers to connect across a network, and emails containing malicious links or attachments.
Another way of getting this malware is through drive-by downloading. Drive-by downloading is when an unaware user visits an infected website. The computer then downloads malware without the user’s knowledge which will eventually be the ransomware.
In some cases, end-users receive emails which trick the victims into opening an attachment or clicking on a link that contains a malicious file, which then encrypts files on a corporate network or individual PCs. Today, ransomware can also spread through social media and chat apps.
Vulnerable web servers are a common target of these attacks. They are exploited as an entry point to gain the organization’s network access, especially now that accessing these servers is made more possible because of cloud technology.
The first known ransomware attack occurred in 1989 when an AIDS researcher Joseph Popp distributed 20,000 floppy disks to other fellow AIDS researchers in over 90 countries.
Popp claimed that the disks contained a program that analyzed a person’s chance of acquiring the disease by using questionnaire. However, not only a program is inside of the disks but also malware.
The malware was not seen at first but was eventually activated after the 90th time of turning on the computer.
The computer then displayed a message that demands $567 in total for pc activation and software lease. This ransomware attack was named as the AIDS Trojan or the PC Cyborg.
Nearly three decades after the attack, the healthcare industry has been one of the top targets of ransomware attacks. This is because of the insufficiency of healthcare providers to have modern equipment and cyber protection. Another reason for this is the lives at stake when medical data is taken hostage, which makes it more likely that medical practitioners will pay the ransom.
Crypto-based and locker-based attacks have remained as the two district varieties of ransomware.
The difference between the two is that crypto-based ransomware encrypts files, folders, and hard drives, whereas locker-based ransomware locks users out of their devices.
Now, new-age ransomware distributes new strains of malware and develops at an alarming rate. These attacks now use crypter software to ensure reverse-engineering will not be easy.
Offline encryption methods also became popular nowadays. They take advantage of legitimate system features like Microsoft’s CryptoAPI, which removes the need for Command and Control (C2) communications.
There are ways to fight a ransomware attack whenever one happens. Calling the authorities is a great idea, but this might trigger them more. Having the right protection to prevent or recover from such an attack is also a good way not to be victimized by these cybercriminals.
Do not let your business fall once these attacks happen. Read this infographic from Landau consulting to have a better chance in protecting your files.